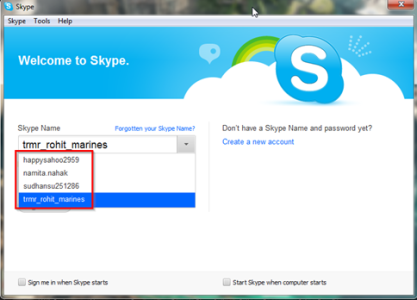
Skype Forensics Tools
Skype synchronizes chats, text messages and files sent and received with the Microsoft Account backend. Accessing Skype conversation histories by performing a forensic analysis of the user’s Microsoft Account is often the fastest and easiest way to obtain valuable evidence. Learn how to use to quickly extract the complete conversation histories along with attachments and metadata from the user’s Microsoft Account. What’s It All About?With over 1.55 billion accounts and more than 420 million daily users, is one of the world’s biggest instant messaging apps.
While there is no lack of competition in the highly crowded market of instant messaging apps, Skype maintains its user base. This feature-rich app is available for all relevant platforms, and is actively developed and frequently updated by Microsoft. Skype is secure (enough) while maintaining transparency to the law enforcement, which makes Skype the only allowed VoIP communication app in countries such as the UAE. The free Skype-to-phone calls included with all Microsoft Office 365 subscriptions help Skype gain popularity among corporate and small office users, while integration with Alexa and Cortana voice assistants makes Skype the tool of choice for voice calls.Skype conversations are automatically synced with the back end along with attachments. While text chats are stored on Microsoft servers indefinitely or until manually deleted by the user, attachments are only kept for the maximum period of 30 days.
After the 30-day retention period, any files users send or received are automatically purged from the server and are no longer accessible. However, Microsoft still retains information about these files (the metadata), allowing experts to find out the name and type of attachments, file sizes, as well as the date and time.Having said that, one can use Microsoft’s own tool to request and view Skype data from the account. However, information returned by the Microsoft’s tool lacks certain data about the chats and files that have been either deleted by the user or purged from Microsoft servers as a space-saving measure. This is why we developed the tools to extract and view all Skype-related information available in the user’s Microsoft Account. Tools to Extract Skype Chats, Attachments and Metadata from Microsoft AccountWe have exactly two tools to be used in connection with Skype data. First, there is, a tool to download Skype conversation histories from Microsoft servers.
Skype is a secure Internet application that provides video/voice calling, instant messaging and many more options for instant communication. Skype works on peer-to peer architecture. It provides encrypted channel (Transport Layer Security) to protect the clients from spiteful activities. Skype is a well-known VoIP app that plays a vital role in today's communication arena. Challenges in Skype Forensics AnalysisSkype uses strong encoding method such as TLS and Secure RTP to manage connection between its servers and clients. As a result, the misuse of Skype platform by cybercriminal to perform phishing, spamming, and other illegitimate activities has increased. It greatly challenges techies in Skype investigation how to decrypt and extract artifacts?All the Android devices including Skype uses Random Access Memory and NAND flash memory to store the actions applied by users.
Skype App Main Db
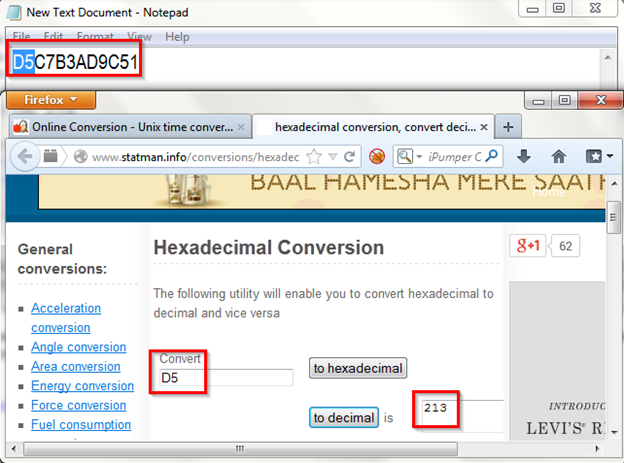
RAM is volatile memory that consists of crucial information like encryption keys, account username and password. Instead, NAND flash memory is nonvolatile. This means, when the system is powered off or rebooted data can recover from NAND flash memory.The aim of this Skype forensics analysis is to identify and extract database from seized device. However, now the question arises:.

What type of data files are generated and stored on the machine?. Location of files?.
Format of the data?. How to view, examine, and retrieve artifacts?In order to answer the aforementioned questions, an investigator needs to perform in-depth analysis and approach to categorize and identify the expected evidence. Let us collect the Skype forensics analysis information via manual File System extraction:. Registry KeysHKEYCURRENTUSERSoftwareSkype.